Recent Phishing Attacks: What You Need to Know
Phishing is a common exploit that is used to steal login credentials. You may have received these types emails in the past and as a savvy web user, were able to avoid falling into these types of traps. Phishing emails come disguised as legitimate or being from a legitimate source saying your password is compromised and you need to change it. You would then be redirected to a login page that appears authentic. Once you complete sign in, your account would be compromised.
John Podesta recently fell victim to a phishing attack and even had confirmation from his IT staff that his Gmail account was in fact hacked and that he needed to change his password immediately. They now say it was a typo, but the reality is that phishing attacks can fool even the most experienced technical users.
The Attack
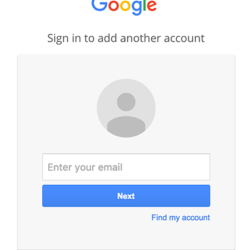
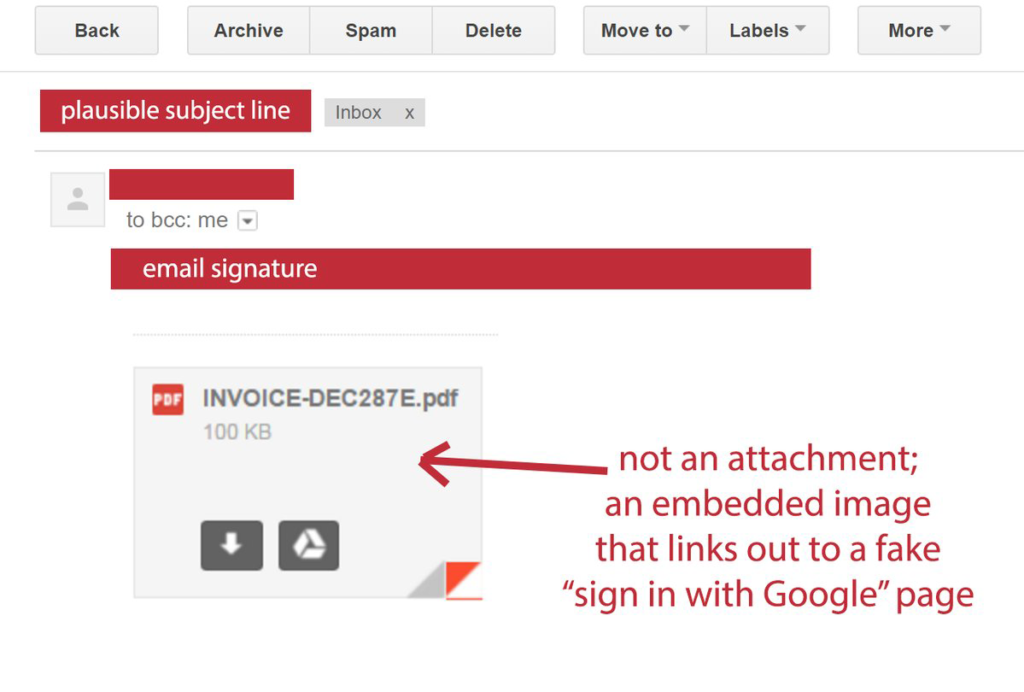
The popular WordPress security plugin Wordfence recently put out a great article about the technical aspects of the attack and how it is fooling users at all experience levels. This attack targets Gmail users specifically and uses image attachments and subject lines from trusted email addresses you already recognize that may have been compromised using the same technique.
What you can do to prevent these types of attacks
As a matter of habit, you should always check the address bar especially when singing into anything to make sure it is in fact a legitimate site. In this case, the url does contain the URL ‘accounts.google.com’, but a closer look reveals additional code.
From the WordFence article:
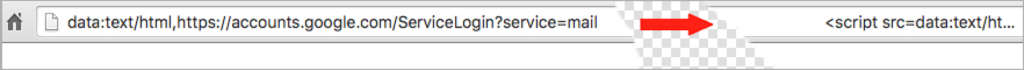
This phishing technique uses something called a ‘data URI’ to include a complete file in the browser location bar. When you glance up at the browser location bar and see ‘data:text/html…..’ that is actually a very long string of text. If you widen out the location bar it looks like this:
There is a lot of whitespace which I have removed. But on the far right you can see the beginning of what is a very large chunk of text. This is actually a file that opens in a new tab and creates a completely functional fake Gmail login page which sends your credentials to the attacker.
As you can see on the far left of the browser location bar, instead of ‘https’ you have ‘data:text/html,’ followed by the usual ‘https://accounts.google.com….’. If you aren’t paying close attention you will ignore the ‘data:text/html’ preamble and assume the URL is safe.
Tom Scott recently tweeted about this same attack that he recieved in his email:
From the WordFence article:
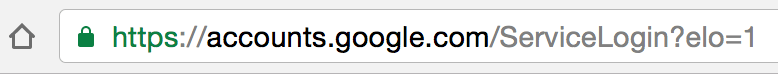
When you sign in to any service, check the browser location bar and verify the protocol, then verify the hostname. It should look like this in Chrome when signing into Gmail or Google:
Make sure there is nothing before the hostname ‘accounts.google.com’ other than ‘https://’ and the lock symbol. You should also take special note of the green color and lock symbol that appears on the left. If you can’t verify the protocol and verify the hostname, stop and consider what you just clicked on to get to that sign-in page.
Enable two factor authentication if it is available on every service that you use. GMail calls this “2- step verification” and you can find out how to enable it on this page.
Enabling two factor authentication makes it much more difficult for an attacker to sign into a service that you use, even if they manage to steal your password using this technique. I would like to note that there is some discussion that indicates even two factor authentication may not protect against this attack. However I have not seen a proof of concept, so I can not confirm this.
How will I know if my account is already hacked?
There is no sure way to know if your account has been hacked. When in doubt, change your password. This is a good practice in general anyway, but will rule out the possibility that someone has access to your account.
In addition, you can check your account activity and see if there has been any suspicious activity: https://support.google.com/mail/answer/45938?hl=en